Managing Cypress Security
This topic describes the types of security available in Cypress and their typical usage, as well as their permission settings. It also provides step-by-step instructions for using the appropriate security tab to set, modify, and remove security permissions.
Overview
Cypress provides a more robust security environment than systems that provide global access rights and permissions only for each user through the Security subtab, which is available by selecting Administration tab in the Administration Tools main window. See Enabling Server-side Security for more information.
Cypress adds another layer of security by providing permissions for each object or module (e.g., a stock or printer definition), which can have its own unique security that you can set on the Security tab for the selected object (i.e., Device). Each object within Cypress has security permissions associated with it. You can define permissions for the users of a specific object. For example, when you create a printer definition named My Printer, you specify to what extent, if any, users can use that printer. See Setting Security Permissions for a Cypress Object.
Although you can use Windows domain security descriptors to control access to Cypress objects, devices, definitions, etc., ASG encourages you to use the Cypress Role feature. Among its many benefits, a role simplifies security as it allows you to control permissions for a Windows domain security user or group related to one or more Cypress objects. In contrast, Windows domain security stores permissions with the object itself, requiring permissions to be managed and maintained object by object. See Defining a Cypress Role for instructions for creating a role.
Setting Cypress Security Permissions
To set Cypress security permissions
- Select the Administration tab in the Administration Tools module.
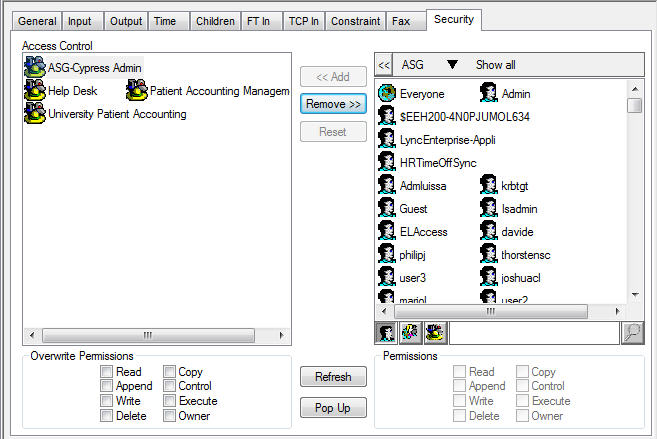
- Navigate to the Security tab of the object or module for which you want to set security, as shown in this example:
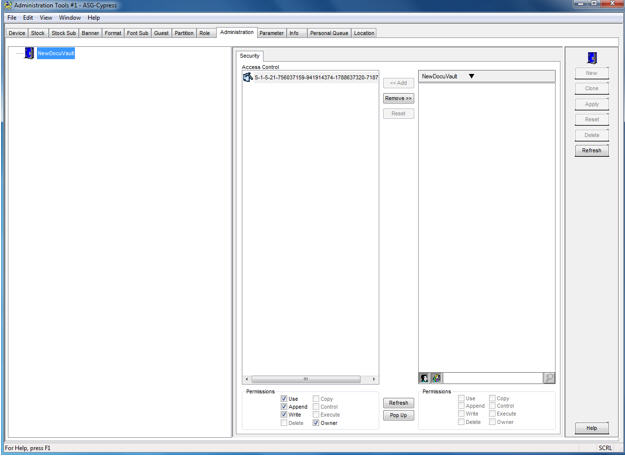
The users in the Access Control list have already been granted permissions for the object or module.
- Select the Windows domain users to add to the Access Control list.
See steps 4 through 10 in Setting Security Permissions for a Cypress Object for instructions.
- Select the appropriate Permission check boxes located below the Domain list (on the lower right portion of the screen). These selections will be applied to the selected domain users when you add them to the Access Control list. You also can edit the permissions for each of the domain users after they have been added to the Access Control list using the check boxes below the Access Control list.
- Click the Add button. The selected domain users will appear in the Access Control list.
- Click the Apply button. Cypress will now apply the security definition to the users in the Access Control list, per their permissions.
- Repeat steps 1 through 6 for all security definitions.
Modifying Cypress Security Permissions
To modify Cypress security permissions
| 1. | On the Access Control list, select the user or users whose permissions you want to edit. |
| 2. | Select or clear the appropriate Permission check boxes located below the Access Control list. |
| 3. | Click the Apply button to save your changes. |
Removing Cypress Security Permissions
To remove a user’s security permissions
| 1. | On the Access Control list, select the user or users whose permissions you want to remove. |
| 2. | Click the Remove button. The selected user(s) will be removed from the Access Control list and reappear in the Domain list. |
| 3. | Click the Apply button to apply the change(s). |
Security Permissions
This table describes the security permissions available on the Security tab:
|
Permission |
Access |
|
Read |
Assignee can see the device in Cypress applications. |
|
Append |
Assignee can queue jobs to the device. |
|
Write |
Assignee can modify defined attributes of the device in the Administration Tools module. |
|
Delete |
Assignee can delete the device definition. |
|
Copy |
Assignee can clone the device definition. |
|
Control |
Assignee can suspend, resume, disable, enable, and change stock on the device as well as modify the job tickets (JTICs) associated with the device, including deleting them. |
|
Execute |
Assignee can copy JTICs queued to a device and paste the copies to a device. |
|
Owner |
Assignee can modify the security defined for the device. |
Setting Security Permissions for a Cypress Object
You can use a Cypress object’s security tab to control the security specific to that object. Typically, end users require only Read and Append—and, in some cases, Control—security permissions. For example, you can specify whether a user can see that a printer exists, print to it, or have any change control over documents in a device queue.
To set security permissions for Cypress objects
| 1. | Launch Administration Tools from the Cypress main window. |
| 2. | Select the tab for the object for which you want to set security (i.e., the Device tab). |
| 3. | Select the Security tab. |
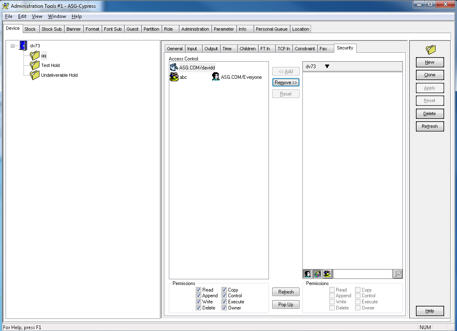
| 4. | Click the downward triangle after the DocuVault name (at top of the right column). |
The available domains for that DocuVault are displayed as a sub-menu.
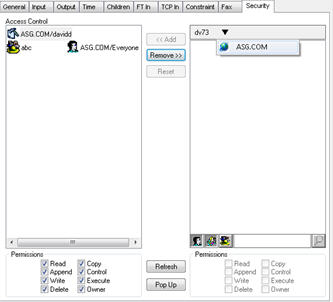
| 5. | Click the button for the domain that you want to select. |
This domain is set on the toolbar at the top of the column following the DocuVault name.
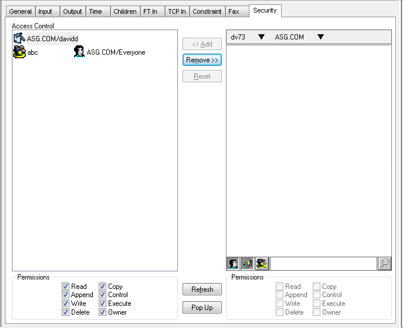
| 6. | Click the downward triangle after the domain name to access a list of available organizational units for that domain. |
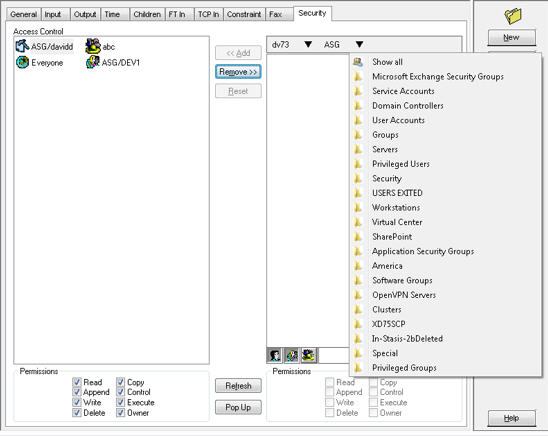
| 7. | Select the Show all option at the top of the list to see all the users in the domain in the list of candidates. |
Or
Select the organizational unit that you want.
The users in that organizational unit are then listed in the column and the organizational unit name is set on the toolbar at the top of the column following the domain name. If a further layer of organizational units is available, another downward triangle follows the organizational unit name.
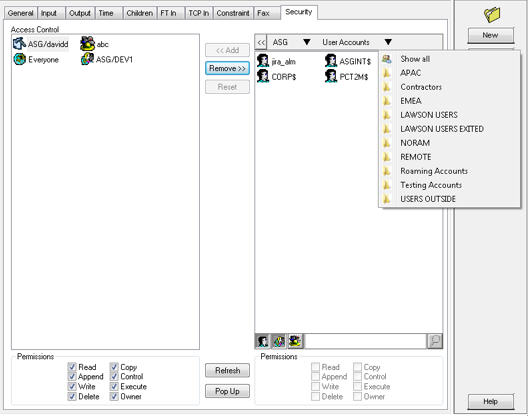
Continue to navigate through the layers of organizational units until you have selected all the users that you want.
| 8. | Optional. If the length of the selected names becomes greater than the length of the toolbar, the first several layers are hidden and a << character is displayed in their place. |
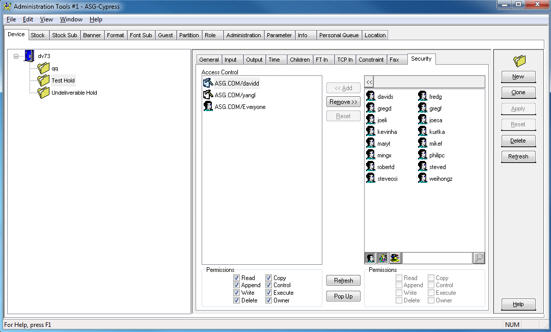
| a. | Click the << button to view the layers that you have selected (DocuVault, domain, organizational units). |
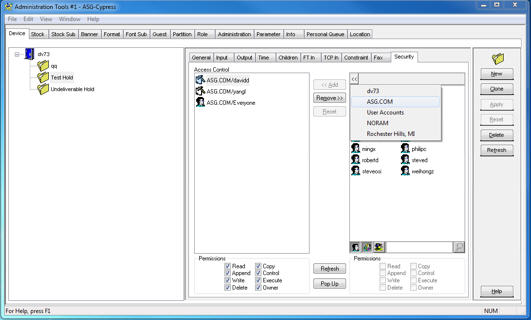
| b. | Click the right triangle next to the last layer displayed (either domain or organizational unit) to see a sub-menu of its organizational units. |
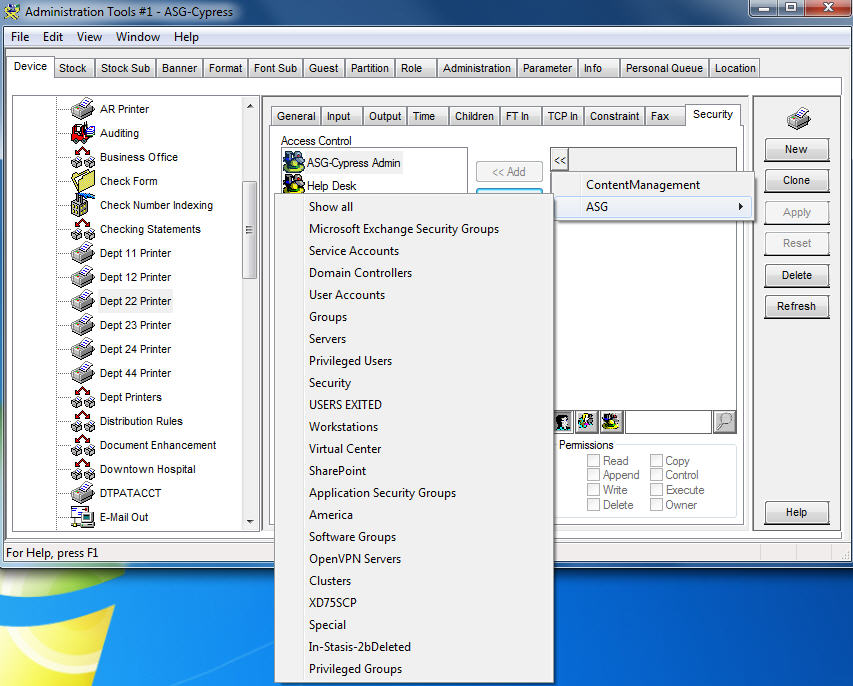
| 9. | Optional. You can choose to use the Search function to navigate through the domain and organizational unit layers. It does not work on the DocuVault layer. |
| a. | Type a search criteria string in the Search field (at the bottom of the right column). You can use an asterisk (*) as a wildcard character. |
| b. | Click the Search button. |
All items in the current layer and sub-organizational unit layers that match the search criteria are shown in the security candidate items list (right column). Once the search criteria is set, the sub-organizational unit layers are no longer shown.
This example shows the results of a search of the ASG.COM domain with the string davids:
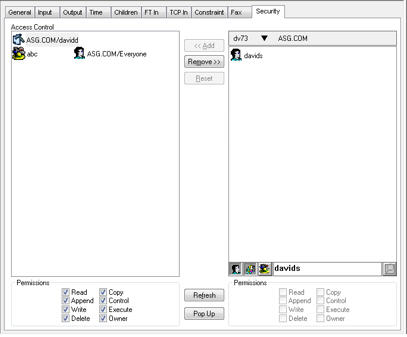
This example shows the results of a search of the ASG.COM domain with the string david*:
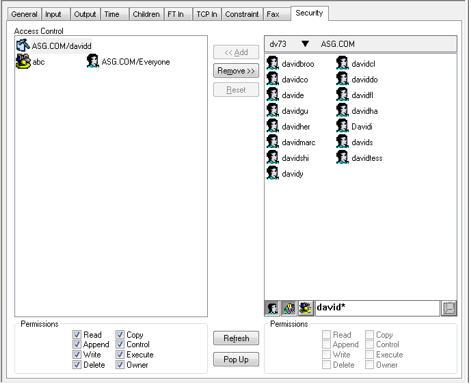
| 10. | Specify the appropriate permissions for the selected users (at the bottom of the right column). See the table in Security Permissions for a description of the security permissions. |
| 11. | Click the Add button. The selected domain users will appear in the Access Control list. |
| 12. | Click the Apply button. Cypress will now apply the security definition to the users in the Access Control list, per their permissions. |
| 13. | Repeat steps 1 through 12 for all security definitions. |
Defining Security Using a Role
Role definitions enable you to create groups of users that you can select when you are defining security requirements for objects (e.g., stocks or printers) within a DocuVault. Instead of adding individual users to each object’s Access Control list (within each object’s Security tab), you simply add groups of users to the object. This simplifies and speeds security management. See Cypress Roles for further information about roles.
You can use roles to assign Windows security to Cypress objects. The role member list contains Windows user IDs and groups along with the permissions that they will inherit when the role is applied to any given object within Cypress. The maximum number of members that can belong to a role is 2,000.
Using role-based security normally makes the administration of security within Cypress easier to maintain. In addition, it allows Cypress to automatically assign page-level security to documents that are being split by predetermined criteria.
Members of the predefined role Super Role have implicit permissions to access every Cypress object, even if they are not explicitly secured to the object.
| • | For documents captured via the DDI protocol, Cypress assigns document security by looking not for guest definitions, but for Cypress roles. Assignment is in this order: |
1) Role with the exact name as the user
2) Role with the exact name as the host machine
3) <default> role
| • | For documents submitted to Cypress via the FT In protocol, Cypress applies to the incoming document the Windows NT file system (NTFS) security settings associated with the specified FT In directory. |
To set security permissions for Cypress roles
| 1. | Click the Role icon at the bottom of the Security tab.  |
Only the DocuVault name is shown on the layer toolbar at the top of the column and unselected roles are listed in the security candidate list.
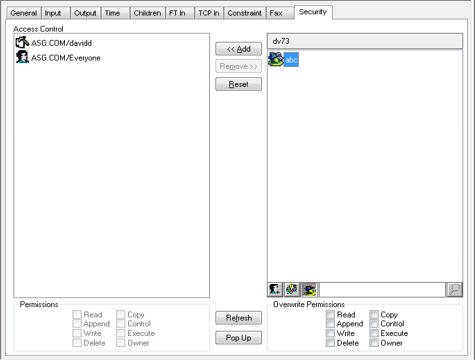
| 2. | Specify the appropriate permissions for the selected role (at the bottom of the right column). See the table in Security Permissions for a description of the security permissions. |
| 3. | Click the Add button. The selected roles will appear in the Access Control list. |
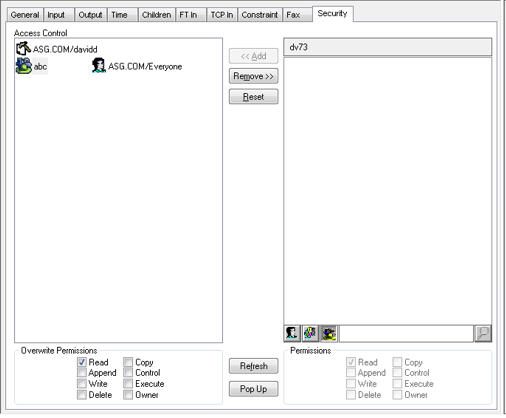
| 4. | Click the Apply button. Cypress will now apply the security definition to the roles in the Access Control list, per their permissions. |
| 5. | Repeat steps 1 through 4 for all security definitions. |
Permission Settings
Each object within Cypress has security permissions associated with it. This section describes the types of security available in Cypress and their typical usage, as well as their permission settings.
Device Security Permissions
You use device security to define who can use or modify a device. This table lists, in order of increasing level of access, the permission settings for using or modifying a device:
|
Permission |
Access |
|
Read |
The user can see the device and all its associated job tickets (JTICs) in Cypress applications. |
|
Append |
The user can queue jobs to the device. |
|
Write |
The user can modify attributes of the device. |
|
Delete |
The user can delete the device definition. |
|
Copy |
The user can clone the device definition. |
|
Control |
The user can suspend, resume, disable, enable, and change stock on the device and can modify the JTICs associated with the device, including deleting them. |
|
Execute |
The user can copy JTICs queued to a device and paste copied JTICs to a device. |
|
Owner |
The user can modify the device’s security settings. |
Permission Assignment
ASG recommends that you assign these device security permissions:
| • | Grant end users Read and Append access. |
| • | Grant print operators Read, Append, Control, and Execute access. |
| • | Grant administrators all permissions. |
Examples
These examples illustrate permissions defined through device security:
| • | To copy a JTIC, a user must have either Copy permission for the JTIC or Execute permission for the queued device. |
| • | To move a JTIC, a user must have either Copy and Delete permission for the JTIC or Control and Execute permission for the queued device. |
| • | To paste a JTIC, a user must have Append or Execute permission for the destination device. |
Stock Security Permissions
You use stock security to define who is allowed to use or modify the selected stock. This table lists, in order of increasing level of access, the permission settings for using or modifying a stock:
|
Permission |
Access |
|
Read |
The user can see the stock in the Administration Tools window. |
|
Write |
The user can modify attributes of the stock. |
|
Delete |
The user can delete the stock definition. |
|
Copy |
The user can clone the stock definition. |
|
Owner |
The user can modify the stock’s security settings. |
Permission Assignment
ASG recommends that you assign these stock security permissions:
| • | Grant end users Read access. |
| • | Grant print operators Read access. |
| • | Grant Report Distribution Manager (RDM) administrators Read access. |
| • | Grant administrators all permissions. |
Stock Substitution Security Permissions
You use stock substitution security to define who is allowed to use or modify the selected stock substitution table. This table lists, in order of increasing level of access, the permission settings for using or modifying a stock substitution table:
|
Permission |
Access |
|
Read |
The user can see the stock substitution tables in the Administration Tools window. |
|
Write |
The user can modify attributes of the stock substitution table. |
|
Delete |
The user can delete the stock substitution table definition. |
|
Copy |
The user can clone the stock substitution table definition. |
|
Owner |
The user can modify the stock substitution table’s security settings. |
Permission Assignment
ASG recommends that you grant print operators Read access and administrators all permissions.
Banner Security Permissions
You use banner security to define who is allowed to use or modify the selected banner. This table lists, in order of increasing level of access, the permission settings for using or modifying a banner:
|
Permission |
Access |
|
Read |
The user can see the banner in the Administration Tools window. |
|
Write |
The user can modify attributes of the banner. |
|
Delete |
The user can delete the banner definition. |
|
Copy |
The user can clone the banner definition. |
|
Owner |
The user can modify the banner’s security settings. |
Permission Assignment
ASG recommends that you assign these banner security permissions:
| • | Grant end users Read access. |
| • | Grant print operators Read and Write access. |
| • | Grant administrators all permissions. |
Format Security Permissions
You use format security to define who is allowed to use or modify the selected format. This table lists, in order of increasing level of access, the permission settings for using or modifying a format:
|
Permission |
Access |
|
Read |
The user can see the format in the Administration Tools window. |
|
Write |
The user can modify attributes of the format. |
|
Delete |
The user can delete the format definition. |
|
Copy |
The user can clone the format definition. |
|
Owner |
The user can modify the format’s security settings. |
Permission Assignment
ASG recommends that you assign these format security permissions:
| • | Grant RDM administrators Read, Write, and Copy access. |
| • | Grant administrators all permissions except Owner. |
Font Substitution Security Permissions
You use font substitution security to define who is allowed to use or modify the selected font substitution table. This table lists, in order of increasing level of access, the permission settings for using or modifying a font substitution table:
|
Permission |
Access |
|
Read |
The user can see the font substitution table in the Administration Tools window. |
|
Write |
The user can modify attributes of the font substitution table. |
|
Delete |
The user can delete the font substitution table definition. |
|
Copy |
The user can clone the font substitution table definition. |
|
Owner |
The user can modify the font substitution table’s security settings. |
Permission Assignment
ASG recommends that you grant print operators Read access and administrators all permissions.
Guest Security Permissions
You use guest security to assign Windows security to documents (and inherently JTICs) captured in Cypress that originated from non-Windows platforms.
| • | For documents captured via the LPD In protocol, Cypress assigns document security by matching defined guests in this order: |
1) Host machine and exact user
2) Host machine and <default> user
3) <default> machine and <default> user
| • | For documents submitted to Cypress via the FT In protocol, Cypress applies to the incoming document the Windows NT file system (NTFS) security settings associated with the specified FT In directory. |
Host Machine Settings
This table lists, in order of increasing level of access, the permission settings for a host machine:
|
Permission |
Access |
|
Read |
The user can see the host name in the Administration Tools window. |
|
Write |
The user can modify attributes of the host. |
|
Delete |
The user can delete the host definition. |
|
Copy |
The user can clone the host definition. |
|
Owner |
The user can modify the host’s security settings. |
User Settings
This table lists, in order of increasing level of access, the permission settings for a user:
|
Permission |
Access |
|
Read |
The user can see the user name in the Administration Tools window. |
|
Write |
The user can modify attributes of the user. |
|
Delete |
The user can delete the user definition. |
|
Copy |
The user can clone the user definition. |
|
Owner |
The user can modify the user’s security settings. |
Permission Assignment
ASG recommends that you assign these guest security permissions:
| • | Grant end users Read access. |
| • | Grant print operators Read access. |
| • | Grant administrators all permissions. |
Partition Security Permissions
You use the partition security to assign security permissions for DocuVault partitions. This table lists, in order of increasing level of access, the permission settings for a user:
|
Permission |
Access |
|
Read |
The user can view documents in the partition. |
|
Write |
The user can modify the selected partition’s description and scheduled deletion time. |
|
Delete |
The user can delete the selected partition. |
|
Owner |
The user can modify partition security. |
Permission Assignment
ASG recommends that you grant end users Read access and administrators all permissions.
Administration Security Permissions
You use the Administration tab on the Administration Tools window to assign Windows security for DocuVault administrators. If a user is a member of Super Role, they do not need to be entered on this tab. The owner of the DocuVault will appear as the owner on the Administration tab. For security purposes, ASG recommends that you add no one else as the owner of the DocuVault.
This table lists, in order of increasing level of access, the permission settings for using or modifying DocuVault settings:
|
Permission |
Access |
|
Use |
For documentation purposes only. This permission provides the Cypress administrator with a place to keep track of Cypress users. |
|
Write |
The user can modify DocuVault parameters. |
|
Append |
The user can create top-level Cypress objects. |
|
Owner |
The user can modify administration security. |
Permission Assignment
ASG recommends that you grant RDM administrators Append access and administrators all permissions.
Job Ticket Security Permissions
You use job ticket security to define who is allowed to access or view the job ticket (JTIC) in Enterprise Output Manager. JTIC security does not affect a document’s long-term archive security.
This table lists, in order of increasing level of access, the permission settings for using or modifying a JTIC:
|
Permission |
Access |
|
Read |
The user can see the document associated with the JTIC. |
|
Write |
The user can modify attributes of the JTIC. |
|
Delete |
The user can delete the JTIC. |
|
Copy |
The user can clone the JTIC. |
|
Owner |
The user can modify the JTIC’s security settings. |
Permission Assignment
ASG recommends that you assign these job ticket security permissions:
| • | Grant end users Read, Write, and Copy access. |
| • | Grant print operators Write and Copy access. |
| • | Grant administrators all permissions. |
Form Security Permissions
You use form security to specify who is allowed to use or modify the selected form. This table lists, in order of increasing level of access, the permission settings for using or modifying a form:
|
Permission |
Access |
|
Read |
The user can see the form in the Resource Manager. |
|
Write |
The user can modify attributes of the form and add databoxes to the form. |
|
Delete |
The user can delete the form. |
|
Copy |
The user can clone the form. |
|
Owner |
The user can modify the form’s security settings. |
Permission Assignment
ASG recommends that you assign administrators all permissions for form security.
Image Security Permissions
You use image security to define who is allowed to view, use, or modify the selected image. This table lists, in order of increasing level of access, the permission settings for using or modifying image security:
|
Permission |
Access |
|
Read |
The user can see the image in Resource Manager. |
|
Write |
The user can modify the description of the image. |
|
Delete |
The user can delete the image. |
|
Copy |
The user can clone the image. |
|
Owner |
The user can modify the image’s security settings. |
Permission Assignment
ASG recommends that you assign administrators all permissions for image security.
Report Group Security Permissions
You use report group security to define who is allowed to view, use, or modify the report group. A user must have access to the report group to have access to any of the reports in the group. Report group security has no effect on document security.
This table lists, in order of increasing level of access, the permission settings for using or modifying a report group:
|
Permission |
Access |
|
Read |
The user can see the report group in the RDM and add reports to the group (if Append permission on the Administration tab has been granted to the user). |
|
Write |
The user can modify the description of the report group. |
|
Append |
The user can copy reports to the report group. |
|
Delete |
The user can delete the report group. |
|
Copy |
The user can clone the report group. |
|
Owner |
The user can modify the report group’s security settings. |
Permission Assignment
ASG recommends that you grant RDM administrators Read access and administrators all permissions.
Report Security Permissions
You use report security to specify who is allowed to view or modify the report. A user must have access to the report to have access to any of its subreports. Report security has no effect on document security.
This table lists, in order of increasing level of access, the permission settings for viewing or modifying a report:
|
Permission |
Access |
|
Read |
The user can see the report in the RDM. |
|
Write |
The user can modify the attributes of the report. |
|
Append |
The user can copy subreports to this report. |
|
Delete |
The user can delete the report. |
|
Copy |
The user can clone the report. |
|
Owner |
The user can modify the report’s security settings. |
Permission Assignment
ASG recommends that you grant RDM administrators Read, Write, and Copy access and administrators all permissions.
Subreport Security Permissions
This topic describes these subreport security options:
| • | View and modification security |
| • | Distribution security |
| • | Destination security |
| • | Document security |
Subreport View and Modification Security
You use subreport view and modification security to define who is allowed to view or modify the subreport. Subreport security has no effect on document security.
This table lists, in order of increasing level of access, the permission settings for viewing or modifying a subreport:
|
Permission |
Access |
|
Read |
The user can see the subreport in RDM. |
|
Write |
The user can modify the attributes of the subreport. |
|
Delete |
The user can delete the subreport. |
|
Copy |
The user can clone the subreport. |
|
Owner |
The user can modify the subreport’s security settings. |
Permission Assignment
ASG recommends that you grant RDM administrators Read, Write, Copy, and Delete access, and administrators all permissions.
Subreport Distribution Security
You use subreport distribution security to specify to whom the subreport can be distributed. Instead of the standard Cypress security user interface, you specify subreport distribution security by selecting or clearing the Only distribute to recipient who has permission to view the document check box on the subreport’s General tab.
| • | If you select this check box, the RDM will check security before it delivers the subreport. Users must have at least Read access to the subreport to receive a job ticket or document ticket, regardless of the recipient’s attributes. |
| • | If you clear this check box, the RDM will not check security before it delivers the subreport. |
Subreport Destination Security
You use subreport destination security to specify who is allowed to access or view the subreport’s job ticket in Enterprise Output Manager. (When the subreport distributes a document, Read and Copy permissions are implicit.) This security has no effect on the security of the archived document.
This table lists, in order of increasing level of access, the permission settings for accessing or viewing a job ticket generated by a subreport:
|
Permission |
Access |
|
Read |
The user can view the job ticket in the Output Manager. |
|
Write |
The user can modify the attributes of the job ticket. |
|
Delete |
The user can delete the job ticket. |
|
Copy |
The user can clone the job ticket. |
|
Owner |
The user can modify the job ticket’s security settings. |
Permission Assignment
ASG recommends that you grant these subreport destination security permissions:
| • | Grant print operators Read, Copy, Write, Control, and Delete access. |
| • | Grant administrators all permissions. |
Subreport Document Security
You use subreport document security to specify who is allowed to access or view the archived document.
This table lists, in order of increasing level of access, the permission settings for accessing or viewing a document generated by a subreport:
|
Permission |
Access |
|
Read |
The user can view the archived document. |
|
Write |
The user can modify the attributes of the archived document. |
|
Delete |
The user can delete the archived document from the DocuVault. |
|
Copy |
The user can copy text from the archived document. |
|
Owner |
The user can modify the archived document’s security settings. |
Permission Assignment
ASG recommends that you assign these subreport document security permissions:
| • | Grant end users Read and Copy access. |
| • | Grant RDM administrators Read, Copy, Write, and Delete access. |
| • | Grant administrators all permissions. |
Bundle Security Permissions
You use bundle security to control who is allowed to access or modify bundle criteria. It does not affect who can view the documents in the bundle.
This table lists, in order of increasing level of access, the permission settings for accessing or modifying a bundle:
|
Permission |
Access |
|
Read |
The user can see the bundle definition in RDM. |
|
Write |
The user can create a sub-bundle for the bundle. |
|
Append |
The user can add a sub-bundle. |
|
Delete |
The user can delete the bundle. |
|
Copy |
The user can clone the bundle. |
|
Owner |
The user can modify the bundle’s security settings. |
Permission Assignment
ASG recommends that you grant RDM administrators and administrators all permissions.
Index Security Permissions
You use index security to specify who is allowed to view or use the index when performing a query from Knowledge Builder or Cypress.Web pages.
This table lists, in order of increasing level of access, the permission settings for viewing or using an index:
|
Permission |
Access |
|
Read |
The user can view and use the index in queries. |
|
Append |
The user can assign the index to documents. |
|
Write |
The user can modify the index’s attributes. |
|
Delete |
The user can delete the index. |
|
Copy |
The user can clone the index. |
|
Owner |
The user can modify the index’s security settings. |
Permission Assignment
ASG recommends that you assign these index security permissions:
| • | Grant end users Read and Append access. |
| • | Grant RDM administrators Read, Append, Write, and Copy access. |
| • | Grant administrators all permissions. |
Document Security Permissions
You use document security to specify who is allowed to view or access a document when performing a query. Document security does not affect document ticket or job ticket security.
This table lists, in order of increasing level of access, the permission settings for viewing or accessing a document:
|
Permission |
Access |
|
Read |
The user can see the document when performing a query. |
|
Write |
The user can modify the document’s attributes. |
|
Delete |
The user can delete the document from the DocuVault. |
|
Copy |
The user can copy text from the document. |
|
Owner |
The user can modify the document’s security settings. |
Permission Assignment
ASG recommends that you assign these document security permissions:
| • | Grant end users Read access. |
| • | Grant RDM administrators Read, Write, Copy, and Delete access. |
| • | Grant administrators all permissions. |
Sticky Note Security Permissions
You use sticky note security to specify who is allowed to view or modify a sticky note. This table lists, in order of increasing level of access, the permission settings for viewing or modifying a sticky note:
|
Permission |
Access |
|
Read |
The user can view the sticky note associated with the document. |
|
Write |
The user can modify the sticky note. |
|
Delete |
The user can delete the sticky note from the document. |
|
Owner |
The user can modify the sticky note’s security settings. |
Permission Assignment
ASG recommends that you assign these sticky note security permissions:
| • | Grant end users Read access. |
| • | Grant RDM administrators Read, Write, and Delete access. |
| • | Grant administrators all permissions. |
E-mail Security Permissions
By default, e-mail security assigns the users listed in the From, To, and Cc fields of the e-mail permission for Read access to the e-mail record and the e-mail attachment document record.
This table lists, in order of increasing level of access, the permission settings for viewing or accessing an e-mail and/or e-mail attachment record:
|
Permission |
Access |
|
Read |
The user can see the e-mail and/or e-mail attachment when performing a query. |
|
Write |
The user can modify the e-mail and/or e-mail attachment’s attributes. |
|
Delete |
The user can delete the e-mail and/or e-mail attachment from the DocuVault. |
|
Copy |
The user can copy text from the e-mail and/or e-mail attachment. |
|
Owner |
The user can modify the e-mail and/or e-mail attachment’s security settings. |
Permission Assignment
ASG recommends that you assign these e-mail security permissions:
| • | Grant end users Read access. |
| • | Grant RDM administrators Read, Write, Copy, and Delete access. |
| • | Grant administrators all permissions. |
Inbox Security Permissions
You use inbox security to specify who is allowed to view or access the document tickets in the Inbox Viewer and Cypress.Web CypressInbox pages, as well as who is allowed to modify the Inbox itself.
This table lists, in order of increasing level of access, the permission settings for viewing, accessing, or modifying an Inbox:
|
Permission |
Access |
|
Read |
The user can see the document tickets in the Inbox. |
|
Write |
The user can modify the Inbox’s attributes. |
|
Delete |
The user can delete document tickets from the Inbox. |
|
Control |
The user can modify the status of document tickets in the selected Inbox. |
|
Owner |
The user can modify the Inbox’s security settings. |
Permission Assignment
ASG recommends that you grant end users Read, Write, Delete, and Control access and administrators all permissions.
Recipient Security Permissions
You use recipient security to specify who is allowed to view and modify a recipient. This table lists, in order of increasing level of access, the permission settings for viewing or modifying a recipient:
|
Permission |
Access |
|
Read |
The user can see the recipient in the Address Book. |
|
Append |
The user can route documents to the recipient. |
|
Write |
The user can modify the recipient’s attributes. |
|
Delete |
The user can delete the recipient. |
|
Copy |
The user can clone the recipient. |
|
Owner |
The user can modify the recipient’s security settings. |
Permission Assignment
ASG recommends that you assign these recipient security permissions:
| • | Grant end users Append access. |
| • | Grant RDM administrators Read and Append access. |
| • | Grant administrators all permissions. |
Recipient Identity Security
By adding and removing user names from the NT Logon Name field on the recipient’s Identity tab, you can control which users Cypress associates with a recipient.
Recipient Inbox Security
You use recipient Inbox security to specify who is allowed to access or modify the document tickets in the Inbox Viewer and Cypress.Web CypressInbox pages.
This table lists, in order of increasing level of access, the permission settings for accessing or modifying a recipient Inbox:
|
Permission |
Access |
|
Read |
The user can see the document tickets in the Inbox. |
|
Write |
The user can modify the Inbox’s attributes. |
|
Delete |
The user can delete document tickets from the Inbox. |
|
Control |
The user can modify the status of the document tickets in the Inbox. |
|
Owner |
The user can modify the Inbox’s security settings. |
Permission Assignment
ASG recommends that you assign these recipient Inbox security permissions:
| • | Grant end users Read access. |
| • | Grant RDM administrators Read, Write, and Control access. |
| • | Grant administrators all permissions. |
Recipient Inbox Deletion Security
The Allow Delete By Owner from Inbox Viewer check box on the General tab of an Inbox’s Properties dialog determines who can delete the Inbox from the Inbox Viewer.
| • | If you select this check box, any user listed on the recipient’s Identity tab can delete the Inbox. |
| • | If you clear this check box, only users granted Owner permission on the recipient’s Security tab can delete the Inbox. |
Attribute Security
You use attribute security to specify who is allowed to subscribe to or access an attribute. These permissions control the extent to which the current recipient can modify or create attribute names within their own recipient definition. The current recipient must have Write permission on the recipient’s Security tab to access the Attribute Name security control. If the current recipient does not have Write permission, the Padlock icon is enabled.
This table lists, in order of increasing level of access, the permission settings for subscribing to or accessing an attribute:
|
Permission |
Access |
||||||
|
Read |
The user can see this attribute in the Address Book.
|
||||||
|
Append |
The user can add a value to the attribute. |
||||||
|
Write |
The user can modify the Set all values subscribable check box. |
||||||
|
Delete |
The user can delete the attribute. |
||||||
|
Owner |
The user can modify the attribute’s security settings. |
Permission Assignment
ASG recommends that you grant end users Read and Append access, and administrators all permissions.
Attribute Value Security
You use attribute value security to specify who is allowed to subscribe to or access an attribute value. These permissions control the extent to which the current recipient can modify their own values. The current recipient must have Write permissions on the Security tab to access the attribute value security control. If the recipient does not have Write permission, the Padlock icon is disabled.
This table lists, in order of increasing level of access, the permission settings for subscribing to or accessing an attribute value:
|
Permission |
Access |
|
Read |
The user can see the value in the Address Book. |
|
Write |
The user can modify the Set all values subscribable check box. |
|
Delete |
The user can delete the attribute value. |
|
Owner |
The user can modify the attribute value’s security settings. |
Permission Assignment
ASG recommends that you assign these attribute value security permissions:
| • | Grant end users Read and Write access. |
| • | Grant RDM administrators Read, Write, and Delete access. |
| • | Grant administrators all permissions. |
Image Queue Security Permissions
You use image queue security to specify who is allowed to use or modify the selected image queue in the Personal Imaging Module. This table lists, in order of increasing level of access, the permission settings for using or modifying an image queue:
|
Permission |
Access |
|
Read |
The user can view the image queue’s properties. |
|
Append |
The user can see the image queue when moving or creating a batch. |
|
Write |
The user can modify the image queue’s properties. |
|
Delete |
The user can delete the image queue. |
|
Copy |
The user can clone the image queue. |
|
Owner |
The user can modify the image queue’s security settings. |
Permission Assignment
ASG recommends that you assign these image queue security permissions:
| • | Grant end users Read and Append access. |
| • | Grant scan operators Read and Append access. |
| • | Grant administrators all permissions. |
Batch Security Permissions
You use batch security to specify who is allowed to use or modify the selected batch. This table lists, in order of increasing level of access, the permission settings for using or modifying a batch:
|
Permission |
Access |
|
Read |
The user can view the batch’s properties. |
|
Execute |
The user can release the batch to a device, queue, recipient, or DocuVault. |
|
Write |
The user can modify the batch’s properties. |
|
Delete |
The user can delete the batch. |
|
Owner |
The user can modify the batch’s security settings. |
Permission Assignment
ASG recommends that you assign these batch security permissions:
| • | Grant end users Read access. |
| • | Grant scan operators Read and Write access. |
| • | Grant administrators all permissions. |
Batch Settings Security Permissions
You use batch settings security to specify who is allowed to use or modify batch settings. This table lists, in order of increasing level of access, the permission settings for using or modifying batch settings:
|
Permission |
Access |
|
Read |
The user can view the batch settings’ properties. |
|
Write |
The user can modify the batch settings’ properties. |
|
Delete |
The user can delete the batch settings. |
|
Copy |
The user can clone the batch settings. |
|
Owner |
The user can modify the batch settings’ security settings. |
Permission Assignment
ASG recommends that you grant scan operators Read access and administrators all permissions.
Page Template Security Permissions
You use page template security to specify who is allowed to use or modify the selected template. This table lists, in order of increasing level of access, the permission settings for using or modifying a page template:
|
Permission |
Access |
|
Read |
The user can view and use the page template (i.e., the template is available when the user clicks the Save As Excel button). |
|
Write |
The user can modify the page template. |
|
Delete |
The user can delete the page template. |
|
Copy |
The user can clone the page template (i.e., the user can use the Save as option to create a new template). |
|
Owner |
The user can modify the page template’s security settings. |
Permission Assignment
ASG recommends that you assign administrators all permissions for page template security.
Role Member Security
The functions granted by permission settings vary from one Cypress object to another. For example, if you grant a user Read permission when you add them to a role, then add that role to an attribute value and a batch, the user will be able to use the attribute value in the Address Book and see the batch’s properties.
Permission Assignment
ASG recommends that you grant end users Read and Append access, and administrators all permissions.
The permissions that you assign when you create a role are only the default permissions. You can override them when you add the role to a particular object.
Role Security
You use role security to specify who is allowed to add and remove members (and their permissions) from a defined Cypress role. This table lists, in order of increasing level of access, the permission settings for adding or removing role security settings:
|
Permission |
Access |
|
Read |
The user can see the role in the list of roles. |
|
Write |
The user can modify attributes of the role. |
|
Delete |
The user can delete the role. |
|
Copy |
The user can clone the role. |
|
Owner |
The user can modify the role’s security settings. |
Permission Assignment
ASG recommends that you grant RDM administrators Read access and administrators all permissions.
Enabling Server-side Security
You can use the Server-side Security option to evaluate all client processes for access permissions to database records in the current DocuVault as well as to enforce whether sensitive information can be accessed, modified, or deleted.
Make sure this list of requirements is met before you use the Server-side Security option:
| • | The Cypress Hub Service is stopped. |
| • | You are a member of the local Administrators or Power Users group. |
| • | The DV Pool option is set in the db_prog utility with no_ddoc_replication as the parameter. |
You use the db_prog utility to enable or disable Server-side Security in the current DocuVault. You also can display the current Server-side Security setting.
To enable Server-side Security
| 1. | Open a command prompt window, and change the working directory to the Cypress Server directory. |
| 2. | Enter this command at the prompt: |
db_prog set_security_check_option enable
To disable Server-side Security
| 1. | Open a command prompt window, and change the working directory to the Cypress Server directory. |
| 2. | Enter this command at the prompt: |
db_prog set_security_check_option disable
To check the current Server-side Security setting
| 1. | Open a command prompt window, and change the working directory to the Cypress Server directory. |
| 2. | Enter this command at the prompt: |
db_prog display_db_status
The current Server-side Security setting displays in the db_prog window.
